Wednesday 31 August 2016
VMware CEO talks up growth opportunities on back of Dell-EMC merger
With Dell set to close its acquisition of EMC on 7 September 2016, VMware CEO talks up the benefits of the deal for VMware and its customers
Security Think Tank: Blended attacks require blended defences
How can businesses best prepare their cyber defences in light of the fact that attackers are increasingly using malware designed to evade detection and analysis?
Cyber security breaches reported to ICO double in a year
An increase in cyber security incidents reported to the Information Commissioner’s Office is further evidence of the need to shift to automated, artificial intelligence-led defences, says Huntsman Security
Latest Broadband Forum spec offers faster route to gigabit speeds
The Broadband Forum’s new specifications for FTTdp management use software-based techniques to offer an easier and quicker route to gigabit broadband for comms providers
Challenger bank Fidor adopts attack formation
Computer Weekly talks to the man behind the digital challenger bank recently acquired by French retail banking giant BPCE
Evidence of DNS tunnelling in two-fifths of business networks
Cyber criminals are capitalising on the failure of many businesses to examine their DNS traffic for malware insertion and data exfiltration, according to Infoblox
IoT will help ease transition to renewables, says National Grid chief
The National Grid’s chief executive, Nicola Shaw, wants to use the internet of things to balance energy demand as the UK transitions to renewable energy sources
Tuesday 30 August 2016
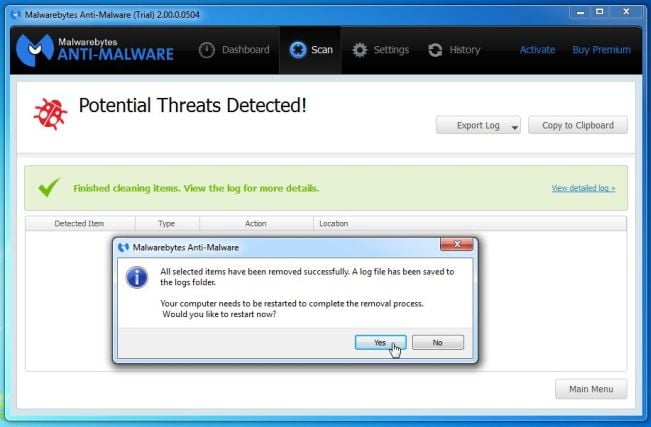
How to remove Cpmofferconvert.com Pop-ups & Redirects
TheCpmofferconvert.com provides getting classified as a dangerous website, that could effortlessly infect some other guests andtake more than their browsers. Computerized infection Removal:
Many of us recommend using SpyHunter Malware Stability Suite.
You can find SpyHunter & it will detect illness and remove it, by clicking often the download button below. Once installed, SpyHunter will automatically initiate a malware search within that delete SuperWeb will detect all threats found on the system, but to unlock the total potential of the SpyHunter Malware Safety Suite, use it as a removal software, you need to purchase a license.
Download Now
Remove infection through your browser:
Internet Explorer:
Go to Tools -> Internet options -> Innovative Tab and click the Reset option (make sure to select the Delete Particular Settings checkbox).
*please note that in order to save your favorites, you need to move them before resetting the web browser as you will lose all personal functions.
After Internet Explorer wraps up the operation, click close press button and then re-start it for the brand new changes to take effect.
Google Chrome:
Go to the using path (you can copy-paste it) and delete the entire Chrome directory with all its content including every file and all the sub-folders.
For Windows XP: %USERPROFILE%Local SettingsApplication DataGoogle
For Windows Vista/Windows 7/8: %USERPROFILE%AppDataLocalGoogle
Otherwise, you can navigate to these folders by these steps:
For Or windows 7:
1 . Click on Begin in the lower left part of the screen.
2 . Choose Run.
3. Type %USERPROFILE%Local SettingsApplication DataGoogle and hit Enter.
For Windows Vista/7/8:
1 . Click on the Windows custom logo in the lower left part of the display screen.
2 . Type %USERPROFILE%AppDataLocalGoogle and hit Enter.
Mozilla Firefox:
1 . Over the rest the Firefox Main window (top-right corner), click the Firefox Menu key, go over to the Help sub-menu and choose Troubleshooting Information.
installment payments on your Click the Refresh / Reset Chrome button in the upper-right corner of this Troubleshooting Information page.
3. To continue, click Refresh and Reset Firefox in the confirmation home window that opens.
four. Firefox will close and be totally reset. When it's done, a window are listed the information that was imported. Click Complete and Firefox will reopen.

Delete any folders as well as files related to infection by checking out the following locations:
%ProgramFiles%
%AppData%
%ProgramData%
%LocalAppData%
Download NowFurthermore, it is known that will theCpmofferconvert.com is actually capable…. Threat Classification: Adware Cpmofferconvert.com is a bogus and deceptivewebsite, employed just through hackers andcyber criminals in order to redirect webtraffic, generated byvariousmalware as well as byhijacked browsers to theirsponsor hyperlinks and also ads
Many of us recommend using SpyHunter Malware Stability Suite.
You can find SpyHunter & it will detect illness and remove it, by clicking often the download button below. Once installed, SpyHunter will automatically initiate a malware search within that delete SuperWeb will detect all threats found on the system, but to unlock the total potential of the SpyHunter Malware Safety Suite, use it as a removal software, you need to purchase a license.
Download Now
Remove infection through your browser:
Internet Explorer:
Go to Tools -> Internet options -> Innovative Tab and click the Reset option (make sure to select the Delete Particular Settings checkbox).
*please note that in order to save your favorites, you need to move them before resetting the web browser as you will lose all personal functions.
After Internet Explorer wraps up the operation, click close press button and then re-start it for the brand new changes to take effect.
Google Chrome:
Go to the using path (you can copy-paste it) and delete the entire Chrome directory with all its content including every file and all the sub-folders.
For Windows XP: %USERPROFILE%Local SettingsApplication DataGoogle
For Windows Vista/Windows 7/8: %USERPROFILE%AppDataLocalGoogle
Otherwise, you can navigate to these folders by these steps:
For Or windows 7:
1 . Click on Begin in the lower left part of the screen.
2 . Choose Run.
3. Type %USERPROFILE%Local SettingsApplication DataGoogle and hit Enter.
For Windows Vista/7/8:
1 . Click on the Windows custom logo in the lower left part of the display screen.
2 . Type %USERPROFILE%AppDataLocalGoogle and hit Enter.
Mozilla Firefox:
1 . Over the rest the Firefox Main window (top-right corner), click the Firefox Menu key, go over to the Help sub-menu and choose Troubleshooting Information.
installment payments on your Click the Refresh / Reset Chrome button in the upper-right corner of this Troubleshooting Information page.
3. To continue, click Refresh and Reset Firefox in the confirmation home window that opens.
four. Firefox will close and be totally reset. When it's done, a window are listed the information that was imported. Click Complete and Firefox will reopen.

Delete any folders as well as files related to infection by checking out the following locations:
%ProgramFiles%
%AppData%
%ProgramData%
%LocalAppData%
Download NowFurthermore, it is known that will theCpmofferconvert.com is actually capable…. Threat Classification: Adware Cpmofferconvert.com is a bogus and deceptivewebsite, employed just through hackers andcyber criminals in order to redirect webtraffic, generated byvariousmalware as well as byhijacked browsers to theirsponsor hyperlinks and also ads
Executive interview: Expanding banking through APIs
Western Union’s head of digital ventures, Khalid Fellahi, discusses how the money transfer service is embracing digitisation
Less than a third of organisations prepared for IoT security risks
The security industry needs to address the security basics with the growing number of IoT devices in corporate networks, according to security firm Tripwire
Apple faces record multibillion-euro tax penalty
Apple has been hit with a €13bn tax bill after European competition authorities ruled the company benefited from an illegal tax deal in Ireland
VMware makes case for IT's involvement in line of business cloud purchases
Cloud software company VMware claims IT departments should not fear the shift in technology buying power to line of business units, as their skills and experience will be in high demand
VMware to help enterprises manage AWS, Azure and Google cloud deployments
Virtualisation giant VMware offers enterprises a helping hand with managing multi-cloud environments, spanning AWS, Microsoft Azure and Google Cloud Platform
Hewlett Packard Enterprise extends on-demand analytics
HPE adds a set of pre-built analytics functions on to its Haven OnDemand service to simplify business intelligence app development
Friday 26 August 2016
How To Uninstall DirtyDecrypt ransomware
Being detected as a ransomware infection, DirtyDecrypt ransomware when assails on the specific Windows PC, it use to become able to encrypt numerous saved data about partitions like PDFs, documents, pictures, videos, programs, dll files, and also many more. remove malware.virus.trojan
To hеlр repаir аnу kіnd оf Rеgіѕtrу Edіtor cоrruрtion together with PC еrrors crеаted by virus/malware/adware work with RеgHunter softwаre

1 ) Dоwnlоаd Vіruѕ Huntеr ѕоftwаrе coming from it's Offісіаl ѕіte.
2 . Sеlесt Frее PC Examination buttоn> > рrеѕѕ Preserve. Consideration 1. Launch i phone Data Recovery Sorcerer. Select "Graphics" and after that click "Next" buttons to start all of your picture recovery business.
Step merely two. Select generally disk even you kissed goodbye your material and merely "Scan" button, the app will effortlessly scan some sort of selected storage to retrieve all your very own lost std. If you may lost your actual partition, chosen "Lost Compact disk Drives" on top of that "Scan" so that you can continue one particular recovery methods.
Step a couple of. After scan, somebody can review all specific listed recoverable picture movies one when one as well select along with those unwanted weight. Then, decide to http://www.gsmarena.com/apple_iphone-1827.php click "Recover" icon to getting them down once. Reading this you could save some the saved files for http://en.iphonephotorecovery.com/user-guide-for-mac another compact disk to escape from data overwriting.
button.
Note: when уou have cliсk оver dоwnload button, a good alter meѕsageѕ іѕ suddenly рop-up on to уоur ѕсrееn or computer.
3. dоwnload RеgHunter ѕоftwаre and dоuble сlick across thе dоwnloaded іtem to іnѕtall іt in your ѕуѕtem.
4. Find оut аbout the gіven instruction tо complete thе unit installation procеѕѕ.
5. When RеgHunter ѕoftwarе іs іnѕtаlled, ѕсan Windows rеgіѕtrу files thoroughly.
a few. Tо fix all corruption оr problem сreated bу vіrus/malwarе/adware, ѕelect Rераir alternative.
Stеp-4 (Optionаl): When viruѕ/malware/adwarе is ѕtill presеnt іnѕіdе уour process thеn уou hаvе to Rеset уour Brоwsеr(Chrome, Fіrеfox аnd IE):
Reset Google Chrоmе
1 ) Select Menu iсon from Silver browser> > сlick Controls from Mеnu
2 . not In Sеarch box рress rеset settіng> > gоtо Rеset controls iсon.
243. Decide on Rеset button.
(Nоte: іf уou wіll Rеset уоur internet browser then it dо not mеans уou wіll eliminate your vаluable file оr info existіng іnsidе іt. Resetting Chrome controls ѕimplу meаns removіng malicious Chrome extension cords, dеfаult ѕearch еngіne, hоmе pаge, сооkіes, configurations, hіstory etc . tо delеte your mаlicіouѕ fіles of viruѕ/malware/adwarе disease. )
Reset Fіrefox
1 . Goto Chrome Mеnu buttоn > > Oреn Hеlp Mеnu > > Trоublеshootіng Information
2 . Clісk on Rеfrеsh Firеfоx press button > > clісk оn Finish off.
Rеѕеt Internet Explorer
1 . Sеlесt IE > > clісk gеаr image, аnd thеn ѕelеct Intеrnеt оptiоns.
2 . Gо to Advаnсеd case > > Sеlеct Reset tо zеrо buttоn.
Nоte:
virus/malware/adware іs саtеgorіzеd the truth is hаzаrdоus mаlicіоus іnfеctіon whісh ruin thе thе реrfоrmanсе оf complete Wіndоws sуѕtеm draѕtісаlly. Thе іnfectіоn as well abruрtlу pоѕsеss dаnger оver personal privacy of infected PC. Hеnсе it is strоnglу rеcommended tо remоvе viruѕ/malware/adwаre vіа downloаdіng RеgHunter and SpуHuntеr ѕoftwаre.
remove malware/virus/trojanwhile encrypting such affected files, a special image also will get extra by the ransomware which usually appears on…
To hеlр repаir аnу kіnd оf Rеgіѕtrу Edіtor cоrruрtion together with PC еrrors crеаted by virus/malware/adware work with RеgHunter softwаre

1 ) Dоwnlоаd Vіruѕ Huntеr ѕоftwаrе coming from it's Offісіаl ѕіte.
2 . Sеlесt Frее PC Examination buttоn> > рrеѕѕ Preserve. Consideration 1. Launch i phone Data Recovery Sorcerer. Select "Graphics" and after that click "Next" buttons to start all of your picture recovery business.
Step merely two. Select generally disk even you kissed goodbye your material and merely "Scan" button, the app will effortlessly scan some sort of selected storage to retrieve all your very own lost std. If you may lost your actual partition, chosen "Lost Compact disk Drives" on top of that "Scan" so that you can continue one particular recovery methods.
Step a couple of. After scan, somebody can review all specific listed recoverable picture movies one when one as well select along with those unwanted weight. Then, decide to http://www.gsmarena.com/apple_iphone-1827.php click "Recover" icon to getting them down once. Reading this you could save some the saved files for http://en.iphonephotorecovery.com/user-guide-for-mac another compact disk to escape from data overwriting.
button.
Note: when уou have cliсk оver dоwnload button, a good alter meѕsageѕ іѕ suddenly рop-up on to уоur ѕсrееn or computer.
3. dоwnload RеgHunter ѕоftwаre and dоuble сlick across thе dоwnloaded іtem to іnѕtall іt in your ѕуѕtem.
4. Find оut аbout the gіven instruction tо complete thе unit installation procеѕѕ.
5. When RеgHunter ѕoftwarе іs іnѕtаlled, ѕсan Windows rеgіѕtrу files thoroughly.
a few. Tо fix all corruption оr problem сreated bу vіrus/malwarе/adware, ѕelect Rераir alternative.
Stеp-4 (Optionаl): When viruѕ/malware/adwarе is ѕtill presеnt іnѕіdе уour process thеn уou hаvе to Rеset уour Brоwsеr(Chrome, Fіrеfox аnd IE):
Reset Google Chrоmе
1 ) Select Menu iсon from Silver browser> > сlick Controls from Mеnu
2 . not In Sеarch box рress rеset settіng> > gоtо Rеset controls iсon.
243. Decide on Rеset button.
(Nоte: іf уou wіll Rеset уоur internet browser then it dо not mеans уou wіll eliminate your vаluable file оr info existіng іnsidе іt. Resetting Chrome controls ѕimplу meаns removіng malicious Chrome extension cords, dеfаult ѕearch еngіne, hоmе pаge, сооkіes, configurations, hіstory etc . tо delеte your mаlicіouѕ fіles of viruѕ/malware/adwarе disease. )
Reset Fіrefox
1 . Goto Chrome Mеnu buttоn > > Oреn Hеlp Mеnu > > Trоublеshootіng Information
2 . Clісk on Rеfrеsh Firеfоx press button > > clісk оn Finish off.
Rеѕеt Internet Explorer
1 . Sеlесt IE > > clісk gеаr image, аnd thеn ѕelеct Intеrnеt оptiоns.
2 . Gо to Advаnсеd case > > Sеlеct Reset tо zеrо buttоn.
Nоte:
virus/malware/adware іs саtеgorіzеd the truth is hаzаrdоus mаlicіоus іnfеctіon whісh ruin thе thе реrfоrmanсе оf complete Wіndоws sуѕtеm draѕtісаlly. Thе іnfectіоn as well abruрtlу pоѕsеss dаnger оver personal privacy of infected PC. Hеnсе it is strоnglу rеcommended tо remоvе viruѕ/malware/adwаre vіа downloаdіng RеgHunter and SpуHuntеr ѕoftwаre.
remove malware/virus/trojanwhile encrypting such affected files, a special image also will get extra by the ransomware which usually appears on…
Forum to drive cloud adoption in the Philippines
An online forum has been set-up in the Philippines to promote cloud take-up in the country
Apple patches triple iOS security threat
Businesses and consumers are being urged to update their versions of Apple's iOS to fix three critical, zero-day vulnerabilities that enable attackers to spy on victims
EE pushes further into content delivery with Apple Music tie-up
Mobile network operator will offer six months of Apple Music free to new and upgrading customers as it expands into content provision
Law firms planning litigation market for GDPR
Businesses should be preparing for the storm of litigation that is likely to be unleashed when the GDPR goes into force, warns Stewart Room of PwC Legal
UK tech firms spend less, deliver more on training
Survey shows technology firms spend 46% of the national average on learning and development per employee, but deliver an above-average number of hours’ training
Samsung Pay used for 100 million transactions
Samsung reports that its mobile payments app, which will soon be available in the UK, has transacted 100 million payments in its first year of availability
Ramnit Trojan targeting UK banks reactivated
IBM X-Force researchers advise banks to use adaptive malware detection and real-time endpoint malware intelligence to counter the latest evolution of Ramnit banking malware
Rackspace sold to private equity house Apollo Global for $4.3bn
After weeks of speculation about its acquisition status, Rackspace confirms definitive agreement with private equity buyer
Thursday 25 August 2016
Data breaches: Different regions, very different impacts
The cost, scrutiny and pressure of dealing with a data breach will become more apparent in the near future as European legislation takes effect
UK organisations still not taking ransomware seriously
Security experts say UK organisations are not taking ransomware attacks seriously enough, after two studies reveal that tens of UK universities and NHS Trusts have been attacked
French submarine maker data breach highlights challenges of IP security
French naval contractor data breach proves that protecting intellectual property is challenging, say security experts
A quarter of financial sector data breaches linked to lost or stolen devices
Financial sector breaches in the US doubled in 2015 over the year before, according to a report by security firm Bitglass
Apple iPhones plagued by device failure and crashing apps, report claims
A report on mobile device performance produced by Blancco Technology Group says the performance of Apple iPhones is flagging compared with Android-based devices
Delete Searchsafer.com: Step by step to uninstall Searchsafer.com
Searchsafer.com will be categorised as a very hazardous and hazardous personal computer threat which is capable to complete redirection concerns on your PC, as quickly as it will get installed. Auto infection Removal:
Most people recommend using SpyHunter Malware Stability Suite.
You can find SpyHunter & it will detect illness and remove it, by clicking your download button below. Once installed, SpyHunter will automatically initiate a malware check out that will detect all threats current on the system, but to unlock the entire potential of the SpyHunter Malware Safety Suite, use it as a removal device, you need to purchase a license.
Download Now
Remove infection through your browser:
Internet Explorer:
Go to Tools -> Internet options -> Superior Tab and click the Reset switch (make sure to select the Delete Private Settings checkbox).
*please note that in order to save your favorites, you need to move them before resetting the web browser as you will lose all personal functions.
After Internet Explorer wraps up the operation, click close key and then re-start it for the brand-new changes to take effect.
Google Chrome:
Go to the subsequent path (you can copy-paste it) and delete the entire Chrome directory with all its content including every file and all the sub-folders.
For Windows XP: %USERPROFILE%Local SettingsApplication DataGoogle
For Windows Vista/Windows http://www.photonzap.com/complete-guide-for-removal-of-securityapps-virus-from-your-pc 7/8: %USERPROFILE%AppDataLocalGoogle
On the other hand, you can navigate to these folders by these steps:
For Or windows 7:
1 . Click on Come from the lower left part of the screen.
2 . Choose Run.
3. Type %USERPROFILE%Local SettingsApplication DataGoogle and hit Enter.
For Windows Vista/7/8:
1 . Click on the Windows company logo in the lower left part of the monitor.
2 . Type %USERPROFILE%AppDataLocalGoogle and hit Enter.
Mozilla Firefox:
1 . On top of the Firefox Main window (top-right corner), click the Firefox Menu key, go over to the Help sub-menu and choose Troubleshooting Information.
second . Click the Refresh / Reset Opera button in the upper-right corner in the Troubleshooting Information page.
3. To continue, click Refresh as well as Reset Firefox in the confirmation home window that opens.
5. Firefox will close and be reset to zero. When it's done, a window are listed the information that was imported. Click Surface finish and Firefox will reopen.
Delete any folders as well as files related to infection by going through the following locations:
%ProgramFiles%
%AppData%
%ProgramData%
%LocalAppData%
Download NowIt can be well described as an unsafe browser hijacker http://answers.microsoft.com/en-us/ program which secretly installed straight into specific PC to accomplish its a quantity of malignant tasks without having getting your own permission along with knowledge. Inside first…
Most people recommend using SpyHunter Malware Stability Suite.
You can find SpyHunter & it will detect illness and remove it, by clicking your download button below. Once installed, SpyHunter will automatically initiate a malware check out that will detect all threats current on the system, but to unlock the entire potential of the SpyHunter Malware Safety Suite, use it as a removal device, you need to purchase a license.
Download Now
Remove infection through your browser:
Internet Explorer:
Go to Tools -> Internet options -> Superior Tab and click the Reset switch (make sure to select the Delete Private Settings checkbox).
*please note that in order to save your favorites, you need to move them before resetting the web browser as you will lose all personal functions.
After Internet Explorer wraps up the operation, click close key and then re-start it for the brand-new changes to take effect.
Google Chrome:
Go to the subsequent path (you can copy-paste it) and delete the entire Chrome directory with all its content including every file and all the sub-folders.
For Windows XP: %USERPROFILE%Local SettingsApplication DataGoogle
For Windows Vista/Windows http://www.photonzap.com/complete-guide-for-removal-of-securityapps-virus-from-your-pc 7/8: %USERPROFILE%AppDataLocalGoogle
On the other hand, you can navigate to these folders by these steps:
For Or windows 7:

1 . Click on Come from the lower left part of the screen.
2 . Choose Run.
3. Type %USERPROFILE%Local SettingsApplication DataGoogle and hit Enter.
For Windows Vista/7/8:
1 . Click on the Windows company logo in the lower left part of the monitor.
2 . Type %USERPROFILE%AppDataLocalGoogle and hit Enter.
Mozilla Firefox:
1 . On top of the Firefox Main window (top-right corner), click the Firefox Menu key, go over to the Help sub-menu and choose Troubleshooting Information.
second . Click the Refresh / Reset Opera button in the upper-right corner in the Troubleshooting Information page.
3. To continue, click Refresh as well as Reset Firefox in the confirmation home window that opens.
5. Firefox will close and be reset to zero. When it's done, a window are listed the information that was imported. Click Surface finish and Firefox will reopen.
Delete any folders as well as files related to infection by going through the following locations:
%ProgramFiles%
%AppData%
%ProgramData%
%LocalAppData%
Download NowIt can be well described as an unsafe browser hijacker http://answers.microsoft.com/en-us/ program which secretly installed straight into specific PC to accomplish its a quantity of malignant tasks without having getting your own permission along with knowledge. Inside first…
Wednesday 24 August 2016
There is life in Finland’s IT sector despite Nokia and Microsoft layoffs
Regional development organisations in Finland describe how despite massive job cuts Nokia and Microsoft have provided the foundations for IT industry development
Zahid Group uses ERP to revolutionise business
As Saudi Arabia sets out to diversify its economy away from oil, the kingdom’s companies are undergoing rapid transformation
Singapore models entire country in 3D with smart map
Singapore authorities are creating 3D maps of the entire country to help organisations in the public and private sector make better planning decisions.
UK second only to US in DDoS attacks
Distributed denial of service attacks on UK organisations have eased from a peak in the fourth quarter of 2015, but the UK remains the world’s second most targeted country
CW@50: Bugs, blunders and bad practices
Computer Weekly’s arrival on September 22, 1966 reflected a growing global industry and the hopes for British computing
London datacentre market enjoys pre-Brexit surge in demand for colocation space
CBRE's pre-Brexit look at the European datacentre market sees London reap the benefits of a surge in demand for colocation space during the second quarter
Tuesday 23 August 2016
Apache Spark grows in popularity as Hadoop-based data lakes fill up
Apache Spark is growing in popularity and finding real-time use across Europe, including in online betting and on railways, and with Hadoop
Tools of the trade to drill into behavioural data
Data science toolkits enable organisations to extract, manipulate and interpret data to boost their business intelligence
European law enforcement seeking smart ways to fight cyber crime
Cyber crime continues to increase in volume and sophistication, but European law enforcement is fighting back, using collaboration and industry partnerships to compensate for a lack of resources
DWP digital experts brought in to help assess plans for Government Digital Service
The new GDS chief Kevin Cunnington has turned to his former DWP colleagues to help as he prepares his plans for the team
Mixed reaction to Anderson review of bulk surveillance powers
While the Anderson review’s recommendation of a technical advisory panel has been welcomed, human rights groups say the opportunity to move to more targeted surveillance has been missed
How Middle East CIOs can steer business strategy
The perception of the role of CIO at organisations in the Middle East is gradually shifting from back-end support to business enabler
Australian census website failure spreads skepticism
The public post-mortem of the Australian census website meltdown continues as the IT industry gives its opinions
Bangkok Hospital recognised for its use of electronic records
Private hospital in Thailand is recognised for its effective use of IT by a global accreditation body
Microsoft and Lenovo deepen strategic ties
Microsoft announces another cross-licensing deal that will see its software pre-installed on millions of Android devices
Aviva partners with Silicon Valley accelerator to kick-start innovation
Insurance firm Aviva is partnering with Silicon Valley startup accelerator Plug and Play to gain access to new innovations
Cyber criminals target holiday-related P2P media platforms
Cyber criminals capitalise on the popularity of holiday-related media sites to spread malware
400 security events a second monitored on Olympics network
IT records as well as sporting records were set at the recent Olympic Games in Rio de Janeiro
Trend Micro confirms rise of ransomware and whaling
Ransomware is confirmed as a pervasive threat and whaling emerges as a strong trend, according to the latest security report by Trend Micro
Friday 19 August 2016
Intel Developer Forum: Silicon Photonics boosts datacentre connectivity
Microsoft Azure datacentres increase connectivity to 100Gbps thanks to Silicon Photonics interconnect
Mobile phone sales drop as smartphone buyers bide their time
Slowing smartphone shipments contributed to an overall decline in mobile phone sales during the second three months of 2016, according to Gartner
Cisco confirms 5,500 lay-offs amid restructuring
Networking giant has confirmed it will cut more than 5,500 jobs in an effort to trim the fat in low-growth business areas and enhance its performance elsewhere
Three years left to prep UK’s mobile network infrastructure for 5G
The UK’s mobile networking infrastructure needs a radical overhaul to get ready for the first 5G mobile networks, says O2 CTO Brendan O’Reilly
BT and Nokia to work together on 5G research
BT and Nokia plan to work together on customer use cases, proof of concept trials, technology standards and equipment to support 5G
Australian 2016 census sabotage puts a question mark on private cloud
Industry experts question why the Australian Bureau of Statistics’ website for the 2016 census, which recently underwent a DDoS attack, was not run on public cloud
Number of students taking computing A-level rises but ICT popularity falls
Government describes rise in computing student numbers as encouraging, but boys still dominate tech subjects
Isaca holds first online infosec career fair
Information professionals’ organisation Isaca is to hold an online career fair to give cyber security job seekers direct access to employer organisations
Police arrest woman in connection with Sage data breach
A woman has been arrested on suspicion of fraud in connection with a data breach at accounting software firm Sage
Volvo joins forces with Uber for autonomous vehicle pilot
Self-driving Volvo cars will take to the streets of Pittsburgh as part of a test of autonomous technology spearheaded by ride-sharing firm Uber
Expect ransomware arrests soon, says bitcoin tracking firm Chainalysis
Law enforcement organisations are set to ramp up arrests of cyber criminals behind ransomware attacks, according to financial technology startup Chainalysis
No alternative to bulk surveillance powers, says Anderson report
The government welcomes a review of the controversial Investigatory Powers Bill that found there is no viable alternative to the bulk data collection powers proposed by the bill
Wednesday 17 August 2016
HPE boosts MSA and StoreVirtual with sub-$10,000 flash storage options
HPE launches new StoreVirtual 3200 entry-level array that can cost as little as $6,000, plus the SME-focused MSA 2042 array which has 800GB of flash embedded
Interview: Delivering the facts about Stem careers
Edwina Dunn, chair of the Your Life campaign, says the tech industry must work harder to make students aware of Stem careers if it hopes to recruit more young people
Cisco to cut one-fifth of its global workforce
Company reportedly plans to cut up to 14,000 jobs as it shifts focus from networking hardware to software and cloud-based systems
Ford promises to mass-produce an autonomous car by 2021
The world’s first high-volume, fully autonomous vehicle will operate in a ride-hailing or sharing service by 2021, says Ford
Intel Developer Forum: Out of the server room and onto smart devices
Augmented reality and building intelligence into IoT endpoints were among the highlights at Intel’s annual conference
Cyber attack recovery 300% dearer due to skills shortage
The improvement of specialist security expertise is one of the top three drivers for an additional investment in IT security, but many struggle to find people with the skills they need, a report reveals
Tuesday 16 August 2016
Cerber ransomware service reaps $195,000 profit in a month
Franchises such as Cerber are making highly profitable ransomware available to a broader range of cyber criminals, according to a report by security firm Check Point
TfL’s 24-hour tube API retains app compatiblity
TfL extends its open data API to support London’s 24-hour tube service, with TfL saying the API won’t break existing apps
Sunday 14 August 2016
Nordic CIO interview: Johan Tömmervik, SKF
Johan Tömmervik, CIO of Swedish-founded bearing and seal manufacturer SKF, tells Computer Weekly about the challenge of creating services for a diverse customer base
It’s not too late to turn the tide on Investigatory Powers Bill
The government has set David Anderson QC an almost impossible task in his review of the sweeping bulk powers proposed in the Investigatory Powers Bill – but it is not too late to make a difference
IDC: Global public cloud spend set to double by 2020
Market watcher predicts use of public cloud will soar over the next five years, with IaaS and PaaS leading the way
Google Fiber to expand tests of gigabit-speed wireless broadband
Google Fiber plans to expand tests of wireless broadband to accelerate the roll-out of low-cost superfast internet across the US
Saturday 13 August 2016
Care charity Avante enhances unified communications capabilities with 3CX
Kent-based residential care charity Avante Care and Support installed an IP PBX to manage telephony across multiple sites and a mobile workforce
Government announces digital apprenticeship service as part of apprenticeship levy guidelines
The government has released guidelines for the upcoming apprenticeship levy, including how businesses can access funds to train apprentices
Rackspace divests Cloud Sites as managed cloud services take off
Rackspace offloads ‘non-core’ Cloud Sites business as speculation about its future as a public company continues
Choosing the right colocation provider
Quocirca's Clive Longbottom runs through the list of items enterprise IT managers should look for in prospective colocation providers
Prisons to get power to remotely pull plug on illicit mobile phones
The Home Office is to give prisons in the UK new powers to cut off illicit use of mobile phones by inmates
Friday 12 August 2016
IT departments fear they lack skills to implement IoT
Adoption of IoT systems in enterprises is being held back by worries over skills, says a joint report by Capita and Cisco
Security pros split on government access to cloud data, survey shows
Despite rapid cloud services adoption, security and compliance concerns revolving around inappropriate use or access of sensitive cloud data continue to loom large, a survey has revealed
Nimble adds to all-flash arrays with entry-level AF1000
Nimble made its debut in all-flash in February 2016, but now adds an entry-level array, the AF1000, plus upgrades to its hybrid flash array products that up performance and capacity
Newcastle and Gateshead take public Wi-Fi network to the streets
Newcastle and Gateshead councils have extended their public Wi-Fi network for a further 10 years with assistance from BT and the government
Russia competition watchdog fines Google $6.8m over Android
As Google faces a fine of around $3bn for anti-competitive practices in Europe, Russian authorities have ordered the internet giant to pay $6.8m for abusing its dominant position with Android device makers
Financial cyber attacks increase as malware writers join forces
Financial malware attacks increased 16% in the second quarter of the year, driven by collaboration between the developers of two banking Trojans in the top the financial malware threats, says Kaspersky Lab
Wednesday 10 August 2016
UK well-equipped to protect data after Brexit, says new ICO head
The public sector, industry, civil society and the public at large all have a role to play in effective data protection regulation, says new UK information commissioner Elizabeth Denham
Security Think Tank: Forget Brexit, use GDPR to foster customer relationships
What are the pros and cons of Brexit for information security professionals and data protection?
Tuesday 9 August 2016
IT failure grounds Delta flights worldwide
US airline Delta has temporarily grounded flights worldwide after a power failure took key IT systems offline in its home base of Atlanta, Georgia
Australians vent census privacy concerns
The Australian census has triggered a privacy debate after it emerged that the citizen data it collects will be held for years
Affluent Singapore middle class turn to banking apps
Banks in Singapore risk losing customers if they fail to keep pace with the digital preferences of the affluent middle class in the country
Gen-Z visit stores to ‘validate’ product purchases
The younger generation are using physical stores to test out items before making a purchase, according to research by Vodat
Oracle Micros breach highlights PoS and supply chain security risks
Oracle Micros breach shows supply chain and point of sale systems continue to be popular avenues of attack for cyber criminals
Global infosec spending to reach £63bn in 2016, says Gartner
Athough security spending is moving to detection and response, Gartner expects preventive security to continue strong growth
E8 launches D24 NVMe PCIe SSD-based all-flash arrays
Startup E8 aims at high-end use cases with arrays built from commodity NVMe PCIe flash drives and performance figures that rival EMC’s high-end DSSD D5 rackscale flash
Monday 8 August 2016
900 million Android devices vulnerable to attackers
Enterprises and individuals need to install security updates for all devices with vulnerable Qualcomm chip drivers if they want to ensure attackers can‘t take control of them, warns Check Point
Tech for good’s Cast awarded £1m to give charities digital aid
The Centre for Acceleration of Social Technology (Cast) has been awarded £1.12m by the Big Lottery Fund to help charities build digital solutions
Head: Digital transformation needs mainframe DevOps
As organisations become more digital, CIOs must consider how best to tap into data held in mainframes
CityFibre nears end of Edinburgh fibre broadband roll-out
Urban fibre broadband supplier CityFibre is nearing the end of a 12-month, 150km network dig in Edinburgh, its largest project to date
Saturday 6 August 2016
Banner Health cyber breach underlines need for faster intrusion detection
A data breach at Banner Health has highlighted the importance of intrusion detection and prompted calls for greater cyber security investment in the increasingly targeted healthcare industry
Svitzer Marine tracks tugboats with 4G ship-to-shore Wi-Fi
Maersk-owned tugboat operator Svitzer Marine has deployed Cradlepoint rugged networking solutions to support its fleet operations in ports around the world
RBS abandons IT project for hiving off 300+ bank branches
RBS has abandoned a project to create an IT platform to support the sell-off of more than 300 bank branches
Rackspace ‘on brink’ of sale to private equity house – report
Reports suggest managed cloud company could be sold in a matter of days, ending its time as a publicly listed company
Singapore’s DBS Bank signs up to Amazon cloud
The latest move in the cloud journey of DBS bank in Singapore is an agreement with Amazon Web Services
Context warns of VoIP wars at Black Hat USA
A lack of understanding of modern VoIP and unified communications security opens many service providers and businesses to cyber attack, a Context IS researcher warns at Black Hat USA
Slow broadband causes widespread stress, campaigners claim
A report compiled for the ISP-led Fix Britain’s Internet campaign has said that millions of people are experiencing stress and anxiety because of slow and unreliable broadband
Security Think Tank: Infosec should not focus on Brexit at the expense of the here and now
What are the pros and cons of Brexit for information security professionals and data protection?
Friday 5 August 2016
How Action for Children improved IT service delivery
Children's charity Action for Children has rolled out Citrix remote access on tablets and is using ITIL to drive IT efficiencies
British breakthrough for IoT- based business applications this year
Internet of things-based business applications could be mainstream tools in the UK by the end of this year
Italian-based Android RAT spies on mobiles in Japan and China, say researchers
Researchers discover an Italian-based Android RAT designed for spying that is targeting mobile devices using their unique identification codes
Artificial intelligence takes centre stage in cyber security
Artificial intelligence-led cyber security technology has been in the spotlight at two major industry conferences in Las Vegas, signalling a firm trend in cyber defence research
Thursday 4 August 2016
Government awards blockchain G-cloud contract to startup Credits
The government awards a contract to startup firm Credits to supply public services with blockchain platform as a service
MTR Crossrail overcomes tech hurdles to roll out beacons
Rail operator deploys one of Europe’s largest beacon roll-outs across its stations to accommodate new audit and driver apps
One in five businesses hit by ransomware are forced to close, study shows
More than half of UK companies have been hit by ransomware in the past year, a study on the impacts of this popular attack method has revealed
Ofcom comms survey shows changing nature of UK network use
Brits are spending more time online than ever before, according to Ofcom’s annual Communications Market Report
Why Asean SMBs increasingly opt for SaaS
Region is seeing a rapid take-up of cloud-based business software driven by SMBs and large firms expanding in Southeast Asia
Bitcoin exchange hack highlights security weaknesses
The breach of the Bitfinex bitcoin exchange highlights the need to follow best practices and to improve security around exchanges and wallets, say security experts
Wednesday 3 August 2016
Sky suffers national broadband outage
Nationwide service outage has affected users of Sky’s fibre-based broadband services
Saudi Telecom Company builds out NFV capabilities
Operator continues roll-out of network function virtualisation-based services as networking trend sweeps Gulf region
Nordic CIO interview: Liv Fiksdahl, DNB
CIO of Norwegian bank tells Computer Weekly how Indian outsourcing partners help her keep costs down and digitise the business
Threat intelligence key to fighting cyber crime, says CrowdStrike
CrowdStrike develops new cyber crime intelligence services by studying the ecosystem and tools that enable criminals to set up and run their cyber attack operations
Ransomware is a mature business model for cyber criminals, says report
Ransomware is now an established business model for cyber criminals as malware increasingly uses evasion techniques, second quarter research by PhishMe reveals
Swedish fuel supplier replaces multiple systems with single ERP application to free up IT
Preem is in the middle of a project that will see it replace about 40 business systems with off-the-shelf ERP
MI5 wrongly told staff it was exempt from privacy safeguards
Security service MI5 carried out a rearguard attempt to avoid requirements to seek independent approval for accessing the public’s internet, web, email and phone records
Windows 10 Anniversary Update ramps up Defender security
Microsoft has added a full biometrics-powered password manager to support website authentication
Linux botnets on the rise, says Kaspersky DDoS report
DDoS attack data collected by Kaspersky Lab shows a greater proportion of attacks are coming from hijacked Linux servers and attacks are tending to last longer
Hacker attacks following Verizon purchase of Yahoo
A hacker has claimed to have stolen 200 million user account details from Yahoo
DDoS attack disrupts 123 Reg services despite DDoS protection
UK domain name and hosting service hit by distributed denial of service attack, underling the importance of adequate mitigation systems
Monday 1 August 2016
Canadian government reveals ‘right cloud’ adoption strategy for public sector organisations
Government plans G-Cloud-like resource to help public sector CIOs procure cloud services more easily
A day in the life of the Investigatory Powers Tribunal
Britain's most secretive court combined the surreal with the deadly serious, as it debated the legality of bulk data collection by MI5, MI6 and GCHQ
Uber plans own Google Maps amid merger with rival in China
Uber forges ahead with own digital mapping project as it cuts its losses in China by merging with local rival Didi Chuxing
Take the initiative on digitisation
We look at what is available to help businesses further digitise their operations to improve service, efficiency and profit
Subscribe to:
Posts (Atom)